How ARP Spoofing Attacks Let Hackers Take Control of Your Local Network
When most people think about network security, they imagine hackers breaking through firewalls or cracking complex passwords. But some of the most dangerous attacks happen much closer to home, exploiting fundamental weaknesses in how local networks communicate. ARP spoofing is one of these attacks, and it’s surprisingly effective at giving cybercriminals complete access to your network traffic without you ever knowing.
Understanding ARP spoofing isn’t just for IT professionals anymore. With more people working from home, using public WiFi, and connecting multiple devices to their networks, everyone needs to know how these attacks work and how to protect themselves. This attack method has been around for decades, but it remains one of the most powerful tools in a hacker’s arsenal because it targets a protocol that forms the backbone of local network communication.

What is ARP and Why Does It Matter?
Before diving into ARP spoofing, we need to understand what ARP actually does. ARP stands for Address Resolution Protocol, and it’s responsible for one of the most basic functions in networking: mapping IP addresses to physical MAC addresses.
Think of it like a phone directory for your local network. When your computer wants to send data to another device on the same network, it knows the IP address (like knowing someone’s name), but it needs the MAC address (like knowing their phone number) to actually deliver the data. ARP is the protocol that handles this translation.
Here’s how it works in a normal scenario. Let’s say your laptop wants to send a file to a printer on your home network. Your laptop broadcasts an ARP request to all devices on the network asking “Who has IP address 192.168.1.100?” The printer, recognizing its own IP address, responds with “That’s me, and my MAC address is AA:BB:CC:DD:EE:FF.” Your laptop stores this information in its ARP cache (a temporary memory storage) and uses it to send data directly to the printer.
This system works efficiently and has been a fundamental part of networking since the early days of the internet. The problem is that ARP was designed in a time when security wasn’t a primary concern. The protocol operates on trust, assuming that devices on a local network are honest and won’t lie about their identity. This naive trust is exactly what makes ARP spoofing possible.
How ARP Spoofing Attacks Work
ARP spoofing, also called ARP poisoning or ARP cache poisoning, is a cyberattack where a hacker sends fake ARP messages to a local network. The goal is to associate the attacker’s MAC address with the IP address of another device on the network, typically the default gateway or router.

Let me walk you through a typical ARP spoofing attack. Imagine you’re sitting in a coffee shop using the free WiFi. An attacker on the same network wants to intercept your traffic. Here’s what happens:
First, the attacker identifies the IP address of the router (let’s say 192.168.1.1) and your device’s IP address (192.168.1.50). They then use special software to send fake ARP replies to your device, claiming “I am 192.168.1.1, and my MAC address is XX:XX:XX:XX:XX:XX” (the attacker’s actual MAC address). Your device, trusting this information, updates its ARP cache to reflect this false mapping.
At the same time, the attacker sends fake ARP replies to the router, claiming to be your device. Now both your computer and the router believe they’re communicating directly with each other, but in reality, all traffic is flowing through the attacker’s machine first. This is called a man-in-the-middle attack.
The beauty of this attack from a hacker’s perspective is that it’s completely invisible to the victims. Your internet continues working normally because the attacker forwards your traffic to its intended destination after copying or modifying it. You might not notice any slowdown or disruption, even though someone is reading every piece of data you send and receive.
What makes ARP spoofing particularly dangerous is how easy it is to execute. Free tools like Ettercap, Cain and Abel, and arpspoof are readily available and require minimal technical knowledge to use. A person with basic networking understanding and malicious intent can launch an ARP spoofing attack in minutes.
What Can Hackers Do With ARP Spoofing?
Once an attacker successfully positions themselves in the middle of your network communication, the possibilities for exploitation are extensive and frightening.
The most common goal is traffic sniffing. The attacker can capture all unencrypted data passing through their machine. This includes passwords sent over HTTP, unencrypted email content, files being transferred, and even credentials for various services. While many websites now use HTTPS encryption, not all connections are secure, and not all users verify they’re on secure connections before entering sensitive information.
Session hijacking is another serious threat. Many websites use session cookies to keep you logged in. If an attacker captures these cookies, they can impersonate you on those websites without needing your password. They could access your social media accounts, online banking, email, or any other service where you have an active session.
Data modification takes ARP spoofing to an even more malicious level. Since the attacker controls the flow of traffic, they can alter data packets before forwarding them. They could inject malicious code into websites you visit, redirect you to fake login pages that steal your credentials, or modify file downloads to include malware. This type of attack is particularly insidious because you have no reason to suspect that the content you’re receiving has been tampered with.
Denial of service is another possibility. Instead of forwarding your traffic, an attacker could simply drop packets, effectively disconnecting you from the network or specific services. While less sophisticated than other attacks, it can be used to cause disruption or distract from other malicious activities.
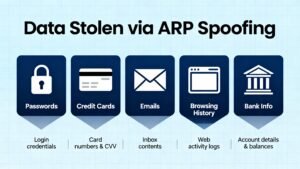
In corporate environments, ARP spoofing can be used for industrial espionage. An attacker on the company network could intercept confidential business communications, steal intellectual property, or gather information about network infrastructure for future attacks. The fact that ARP spoofing happens at the local network level means it can often bypass security measures designed to protect against external threats.
Real World Scenarios and Risk Environments
ARP spoofing attacks are particularly prevalent in certain environments where security measures are relaxed or where multiple unknown users share the same network.
Public WiFi networks are prime targets. Coffee shops, airports, hotels, and libraries offer convenient internet access, but they rarely implement proper security measures. Anyone connected to these networks can potentially launch an ARP spoofing attack against other users. The transient nature of these environments means victims often leave before realizing they’ve been compromised.
Corporate networks, especially larger ones with many employees, are also vulnerable. An insider threat or an attacker who has gained physical access to the building can connect to the network and launch ARP spoofing attacks. In open office environments where visitor access is common, this risk increases significantly.
Home networks aren’t immune either. If your WiFi password is weak or has been compromised, an attacker could join your network and launch attacks against your devices. Smart home devices, which often have poor security, can be compromised and used as launch points for ARP spoofing attacks against other devices on your home network.
Universities and educational institutions present interesting targets. Large campuses often have extensive networks with thousands of users and varying levels of security expertise. Students living in dormitories share network infrastructure, creating opportunities for tech-savvy individuals with malicious intent to experiment with attacks like ARP spoofing.
Even seemingly secure environments can be vulnerable. Co-working spaces, conference venues, and business centers often prioritize convenience over security, making them potential hotspots for network attacks.
Detecting ARP Spoofing Attacks
Detecting ARP spoofing attacks can be challenging because they’re designed to be stealthy, but there are several signs and techniques that can help identify them.
Network administrators can monitor for suspicious patterns in ARP traffic. A sudden flood of ARP replies, multiple devices claiming the same IP address, or frequent changes in MAC-to-IP mappings can all indicate an attack in progress. Network monitoring tools can be configured to alert administrators to these anomalies.
Individual users can check their ARP cache for inconsistencies. On Windows, you can open Command Prompt and type “arp -a” to view your ARP table. On Mac or Linux, the command is similar. If you see multiple devices with the same MAC address or notice your router’s MAC address changing, it could indicate ARP spoofing. However, interpreting these results requires some networking knowledge.
Unexpected network behavior can also be a warning sign. If you notice your internet connection slowing down significantly, websites behaving strangely, or security warnings appearing for sites you trust, these could be symptoms of an ongoing attack. SSL/TLS certificate warnings are particularly important to heed, as they might indicate an attacker is trying to intercept encrypted traffic.
Specialized security software can detect ARP spoofing automatically. Programs like XArp, Arpwatch, and various intrusion detection systems (IDS) continuously monitor network traffic for signs of ARP poisoning and can alert users or administrators when suspicious activity occurs.
For businesses, implementing Security Information and Event Management (SIEM) systems can help correlate data from multiple sources to identify sophisticated attacks. These systems can detect patterns that might not be obvious when looking at individual events.
Protecting Yourself and Your Network
Protection against ARP spoofing requires a multi-layered approach combining technical solutions with user awareness and good security practices.
Static ARP entries are one of the most effective defenses for small networks. By manually configuring ARP entries for critical devices like routers and servers, you prevent devices from accepting fake ARP replies. However, this solution doesn’t scale well for large networks and requires administrative effort to maintain.
Network segmentation significantly reduces ARP spoofing risks. By dividing a network into smaller segments or VLANs (Virtual Local Area Networks), you limit the scope of potential attacks. Even if an attacker compromises one segment, they can’t easily move to other parts of the network.
Dynamic ARP Inspection (DAI) is a security feature available on many enterprise switches. DAI intercepts ARP packets and verifies their legitimacy before allowing them to reach their destination. It maintains a database of valid MAC-to-IP mappings and drops packets that don’t match these bindings.
Port security features on network switches can limit which MAC addresses are allowed to connect to specific switch ports. This prevents unauthorized devices from joining the network and launching attacks. When combined with 802.1X authentication, port security provides robust protection against insider threats.
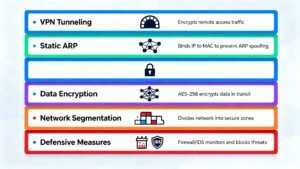
Encryption is your best friend when using untrusted networks. Always use a VPN (Virtual Private Network) when connecting to public WiFi or any network you don’t control. A VPN encrypts all traffic between your device and the VPN server, making intercepted data useless to attackers. Even if someone successfully executes an ARP spoofing attack, they’ll only see encrypted gibberish.
For websites and online services, always verify you’re using HTTPS connections. Most browsers now show a padlock icon in the address bar for secure connections. Never enter sensitive information on websites that don’t use HTTPS, especially on public networks. Browser extensions like HTTPS Everywhere can automatically upgrade connections to HTTPS when available.
Regular software updates are crucial. Operating systems, network drivers, and security software frequently receive patches that address vulnerabilities attackers might exploit. Enable automatic updates whenever possible to ensure you’re protected against known threats.
Intrusion detection and prevention systems (IDS/IPS) provide continuous monitoring and can automatically respond to detected threats. These systems analyze network traffic patterns and can block suspicious ARP activity in real-time.
For home users, keeping your WiFi network secure is essential. Use WPA3 encryption (or WPA2 if WPA3 isn’t available), set a strong password, change your router’s default admin credentials, and keep your router firmware updated. Consider creating a separate guest network for visitors so their devices can’t interact with your main network.
Best Practices for Different User Types
Protection strategies should be tailored to your specific situation and technical capabilities.
For everyday home users, the focus should be on simple but effective measures. Use a reputable VPN service when connecting to any public WiFi. Keep your devices updated with the latest security patches. Use strong, unique passwords for your WiFi network and change them periodically. Be cautious about what information you access when on unfamiliar networks, saving sensitive activities like banking for trusted connections at home.
Small business owners need to invest in proper network infrastructure. Consider managed switches with security features like Dynamic ARP Inspection. Implement network segmentation to separate guest WiFi from business networks. Train employees about network security risks and establish clear policies about device usage. Consider hiring a network security consultant to audit your infrastructure and recommend improvements.
IT professionals and network administrators should implement comprehensive security architectures. Deploy intrusion detection systems and configure them to alert on ARP anomalies. Use network access control (NAC) solutions to verify and authorize devices before granting network access. Regularly audit ARP tables and maintain documentation of authorized devices. Implement logging and monitoring to maintain visibility into network activity.
Remote workers face unique challenges since they often connect to various networks throughout their day. Always use your company VPN when working remotely, even on networks you trust. Consider using a personal hotspot instead of public WiFi for sensitive work. Keep your work devices separate from personal ones when possible. Report any suspicious network behavior to your IT department immediately.
For students and frequent travelers, portability and convenience must be balanced with security. Invest in a reliable VPN subscription. Consider using mobile data for sensitive transactions when public WiFi is your only option. Keep antivirus and anti-malware software updated. Be skeptical of network connection requests and verify network names with staff before connecting.
The Future of ARP Security
As networks evolve, so do both the threats and defenses related to ARP spoofing. Understanding future trends helps us prepare for emerging challenges.
IPv6 adoption is gradually changing the landscape. The newer Internet Protocol version includes IPsec by default and uses Neighbor Discovery Protocol (NDP) instead of ARP. While NDP has its own vulnerabilities, it includes security features that ARP lacks. However, IPv6 adoption remains incomplete, and most networks still rely on IPv4 and ARP.
Zero Trust network architectures are gaining popularity in enterprise environments. These designs assume that threats can exist both inside and outside the network perimeter, requiring continuous verification of every device and user. This approach inherently provides better protection against ARP spoofing since devices must constantly prove their identity.
Software-Defined Networking (SDN) and Network Function Virtualization (NFV) offer new possibilities for dynamic security policies. These technologies allow networks to automatically respond to detected threats, isolating compromised segments or reconfiguring traffic flows to avoid attacks.
Artificial intelligence and machine learning are being integrated into network security tools. These systems can learn normal network behavior patterns and quickly identify anomalies that might indicate ARP spoofing or other attacks. As these technologies mature, detection and response times will improve dramatically.
802.1AE (MACsec) is a Layer 2 security protocol that provides encryption and authentication for Ethernet frames. While not widely deployed yet, MACsec could eventually replace or supplement ARP in securing local network communications.
Conclusion
ARP spoofing remains a potent threat in our interconnected world. Its effectiveness comes from exploiting the fundamental trust built into local network protocols, and its accessibility makes it a tool for both sophisticated cybercriminals and amateur hackers.
The key to protection lies in understanding how these attacks work and implementing appropriate defenses for your situation. Whether you’re an individual user concerned about public WiFi safety, a small business owner protecting customer data, or an IT professional securing corporate infrastructure, the principles remain the same: use encryption, implement network security features, maintain awareness of your environment, and stay informed about emerging threats.
Remember that security is not a one-time fix but an ongoing process. Networks evolve, new vulnerabilities emerge, and attack techniques become more sophisticated. Regular updates, continuous monitoring, and a healthy skepticism about network security are your best defenses.
The good news is that protecting against ARP spoofing doesn’t require expensive solutions or expert-level knowledge. Simple measures like using a VPN, keeping software updated, and being cautious about which networks you trust can dramatically reduce your risk. For organizations, investing in proper network infrastructure and security training pays dividends by preventing breaches before they occur.
As we become increasingly dependent on network connectivity for work, entertainment, and daily life, understanding threats like ARP spoofing becomes more important than ever. By taking security seriously and implementing appropriate protections, we can enjoy the benefits of our connected world while minimizing the risks. Stay informed, stay protected, and never take network security for granted.
Very informative article! The explanations were clear and practical. Cybersecurity is becoming more important every day.
Thanks for breaking it down so well…!